Security today is no longer just about protecting networks or installing the right tools. The way people access systems, applications, and data has become the biggest security risk for most organizations.
Employees work remotely. Vendors need temporary access. Cloud applications sit outside traditional network boundaries. At the same time, attackers are no longer focused on breaking in through firewalls; they target identities instead. Stolen credentials, weak access controls, and excessive permissions are now behind many of the most damaging breaches.
This shift is why Zero Trust security has become a priority for modern organizations. Instead of assuming anything inside the network is safe, Zero Trust treats every access request as untrusted until it is verified.
At the center of this approach is Identity and Access Management (IAM). Identity is no longer just a login system; it determines who can access what, under which conditions, and for how long. When IAM is designed properly, it reduces risk, limits the impact of breaches, and supports compliance without slowing down the business.
In this article, we explore how Identity and Access Management supports Zero Trust security, why identity is now the primary control point for modern environments, and how organizations can strengthen their security posture by focusing on identity first.
Table of Contents
Key Takeaways
- Zero Trust means never trust, always verify every access request must be secure.
- Identity is the foundation of Zero Trust.
- IAM enables strong security through MFA, limited access, and conditional policies.
- Microsoft Entra helps manage identities in Zero Trust.
- Start with MFA, access controls, and device management for a strong foundation.
Why Identity Is the Bedrock of Zero Trust
Zero Trust is often explained as “never trust, always verify,” but in practice, it means something simpler: every access decision should be earned, not assumed.
Identity is what makes this possible.
Instead of trusting a network location or VPN connection, Zero Trust asks basic questions every time access is requested:
- – Who is the user?
- – Is this really them?
- – Is their device safe?
- – Does this Access still make sense right now?
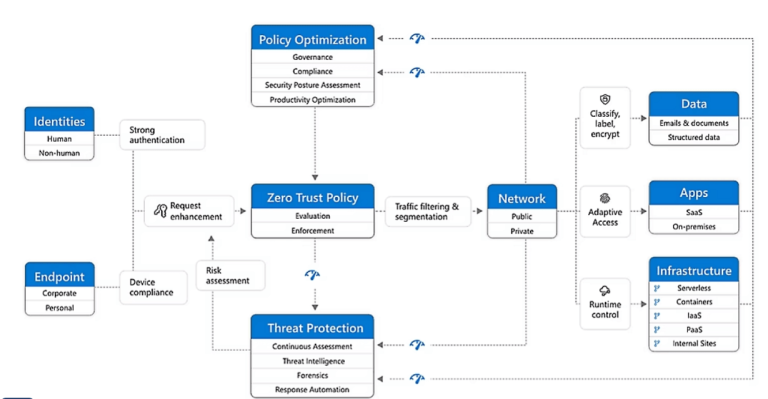
Identity and Access Management provides the answers to those questions. It allows organizations to verify users more than once, limit what they can do, and reduce damage if credentials are compromised.
Without strong identity controls, Zero Trust becomes a slogan instead of a security model.
How Identity and Access Management Powers Zero Trust
So, how exactly does IAM help you build this essential foundation and make Zero Trust a reality? IAM systems provide the tools and policies needed to implement the core principles of Zero Trust across all your digital assets.
1. Explicit Verification
This is the “verify explicitly” pillar of Zero Trust. It means always authenticating and authorizing based on all available data points. Your IAM system is the engine for this. When someone or something tries to access a resource, the IAM system intercepts the request. It doesn’t just check the username and password. It verifies a whole range of signals based on your configured policies:
- – Who is the user (their identity)?
- – Where are they coming from (location)?
- – What device are they using, and is it healthy and compliant with your rules (device compliance)?
- – What are they trying to access (data or application sensitivity)?
- – Are there any unusual behaviors happening (anomalies)? By combining all these signals, IAM helps your system make an informed decision about whether to grant access and how much access to allow.
2. Strong Authentication
A key part of verifying identity explicitly is ensuring that the identity presented is actually the legitimate one. Traditional passwords can be weak or stolen. This is why multifactor authentication (MFA) is absolutely essential in a Zero Trust model. MFA requires users to prove their identity using multiple different methods, like something they know (a password), something they have (a phone or a hardware token), or something they are (a fingerprint). Implementing MFA is often one of the first and most important steps in a Zero Trust journey.
3 Least-Privilege Access
This is another fundamental Zero Trust principle. It means limiting user access to only what they absolutely need to do their job, and only for as long as they need it. This is often referred to as “just-in-time” and “just-enough access “. IAM systems, combined with robust policies, are used to enforce this. By limiting permissions, you significantly reduce the potential damage if an identity is compromised. An attacker who gains access to an account with minimal privileges can’t move around the network as easily or access sensitive data.
4. Conditional Access
IAM enhances security verification through Conditional Access policies. These policies go beyond simply saying “yes” or “no” to access. They allow your system to make dynamic decisions based on the context of the access attempt. For instance, you could set a policy that requires MFA if a user is trying to access sensitive data from an unknown location or an unmanaged device, but allows access with just a password from a trusted device within the corporate network. This adds a layer of risk-based decision-making to access control.
5. Continuous Evaluation
Security isn’t a one-time check. In a Zero Trust world, policies aren’t just enforced when a user logs in. Identity and access policies are enforced at the time of access and continuously evaluated throughout the session. If a user’s risk score changes (perhaps due to a detected anomaly or a change in device health), the system can automatically re-evaluate and potentially revoke or restrict their access in real time.
How Identity Controls Actually Enforce Zero Trust
Zero Trust is not a single product or policy. It is enforced through everyday identity decisions.
Strong authentication ensures users prove who they are, not just once, but whenever risk increases. Least-privilege Access ensures users only see what they truly need, not everything they might want. Continuous evaluation allows Access to change when conditions change.
When identity controls are set up correctly, security becomes adaptive. Low-risk activity feels seamless. High-risk activity triggers additional verification or is blocked entirely.
This balance is what makes Zero Trust usable in real business environments.
Connecting Identity to the Rest of the Digital Estate
Identity doesn’t operate in a vacuum. It’s the glue that connects and secures all the other components of your digital environment in a Zero Trust framework.
Endpoints: Before a user’s device (endpoint) is allowed to access resources, the user’s identity is verified, and the device’s compliance and health status are checked. IAM integrates with device management solutions to ensure this happens.
Applications: IAM ensures that once a user’s identity is verified, they only get the appropriate permissions within the applications they access. Access to applications should be adaptive based on identity and context.
Data: Identity and least-privilege principles are vital for protecting data. Along with classifying and encrypting data, IAM controls who can access sensitive information based on their verified identity and role.
Network & Infrastructure: Access to network resources and underlying infrastructure (like servers or cloud services) is controlled and limited based on identity-driven policies, not just network location.
Microsoft's Role in Identity-Centric Zero Trust
Many organizations turn to established platforms to help implement their Zero Trust strategy. Microsoft, for example, provides a range of tools centered around identity to help verify and secure access across various environments. Microsoft Entra (formerly known as Azure Active Directory) is highlighted as a key solution for managing and securing identities for Zero Trust. Microsoft offers guidance on deploying identity infrastructure and configuring identity and device security policies specifically for Zero Trust.
How Microsoft Entra Supports an Identity-First Zero Trust Approach
Modern identity platforms are built to support this kind of adaptive security. Microsoft Entra brings identity, access policies, and risk signals together in one place.
Conditional Access allows organizations to control Access based on real conditions, not assumptions. A trusted user on a compliant device may sign in smoothly, while the same user on an unmanaged device may be asked for stronger verification or denied Access.
Identity Protection helps detect risky sign-ins early, before they turn into security incidents. Privileged Identity Management limits administrative Access so that powerful roles are only active when truly needed.
These controls work quietly in the background, reducing risk without constantly interrupting users.
Benefits of a Strong Identity Strategy for Zero Trust
Focusing on identity as the core of your Zero Trust implementation brings significant benefits:
- – Reduces the Attack Surface: By verifying every identity and every request, you drastically reduce the number of potential entry points for attackers.
- – Minimizes the Impact of a Breach: Even if an identity is compromised, enforcing least-privilege access limits what the attacker can do and where they can go, containing the damage.
- – Supports Secure Remote and Hybrid Work: With a verified identity and conditional access, users can securely access resources from anywhere on any compliant device.
- – Enhances Visibility and Threat Detection: IAM systems log access attempts, providing valuable data for monitoring and detecting suspicious activity.
Getting Started with Identity in Your Zero Trust Journey
Adopting a full Zero Trust model is a long-term journey, but you can start strong by focusing on identity and device protection. Begin by implementing:
- Multifactor Authentication (MFA)
- Least-Privilege Access
- Conditional Access policies
Pair these with enrolling all devices in a trusted management solution. These steps lay a solid foundation for a secure Zero Trust environment, making it easier to scale and strengthen over time.
What Identity-First Zero Trust Looks Like in Practice
Implementing Zero Trust through identity is not about flipping a switch. It’s a gradual process that starts with visibility and improves over time.
The first step is understanding how identities are actually used. Who has Access? What roles exist? Where are permissions excessive or outdated?
Next comes tightening controls carefully. Authentication is strengthened. Privileged Access is reduced. Risk-based policies are introduced in stages to avoid disruption.
Finally, identity becomes part of daily security operations. Access is reviewed regularly. Risk signals are monitored. Security teams gain confidence that identities are working with them, not against them.
This approach improves security without slowing down the business.
Why Identity and Access Management Breaks Down in the Real World
Most organizations don’t fail at Identity and Access Management because they ignore security. They fail because IAM slowly becomes messy over time.
Users change roles. Contractors come and go. Admin access gets granted “temporarily” and never removed. Service accounts accumulate permissions no one remembers approving. On paper, IAM exists. In practice, it becomes difficult to manage and even harder to trust.
Another common problem is that access decisions are often made only once at sign-in. After that, the session is trusted, even if something changes. The user might switch devices, connect from a risky location, or show unusual behavior. Traditional IAM does not account for this.
Hybrid environments make things worse. Identities are spread across cloud apps, on-prem systems, and third-party platforms. Without centralized visibility, security teams can’t easily see how identities are actually being used or abused.
When IAM is treated as a setup task instead of an ongoing security process, it creates blind spots. These blind spots are exactly what attackers look for.
Identity Security and Compliance Go Hand in Hand
For regulated industries, identity controls are not just a security requirement, they are a compliance necessity.
Auditors want to see clear answers to simple questions:
- – Who had Access?
- – Why did they have it?
- – Was it appropriate?
- – Was it reviewed?
Strong IAM practices make these answers easy to provide. Access logs, role reviews, and identity reports replace manual explanations and spreadsheets.
When identity governance is built into daily operations, compliance becomes part of the system instead of a last-minute scramble.
Conclusion
In today’s world, trust must be redefined. Zero Trust security, built on the principle of “never trust, always verify,” offers the modern framework organizations need to stay secure.
At its core is identity. A strong Identity and Access Management (IAM) strategy with clear verification, strong authentication, least-privilege access, and conditional policies isn’t just part of Zero Trust, it’s the foundation. Prioritizing identity security sets the stage for a more resilient, future-ready defense.
Frequently Asked Questions (FAQs)
Is Identity and Access Management the same as Zero Trust?
No. Identity and Access Management (IAM) is not the same as Zero Trust, but it is the foundation of it. Zero Trust is a security approach, while IAM provides the controls that make Zero Trust possible. Without strong identity verification, access controls, and monitoring, Zero Trust cannot be effectively enforced.
Why is identity considered the biggest security risk today?
Most modern attacks do not start with hacking infrastructure. They start with stolen credentials, weak passwords, or excessive access. Once an attacker gains access through an identity, they can move freely unless identity controls are in place to stop them. That is why identity has become the primary attack surface.
Does Zero Trust mean users are constantly blocked or interrupted?
No. When implemented correctly, Zero Trust actually reduces unnecessary friction. Low-risk users on trusted devices can access systems smoothly, while higher-risk situations trigger additional verification. The goal is to balance security with usability, not slow people down.
Is multi-factor authentication enough to support Zero Trust?
Multi-factor authentication is a critical starting point, but it is not enough on its own. Zero Trust also requires least-privilege access, risk-based policies, identity monitoring, and ongoing access reviews. MFA without proper access governance still leaves gaps.
How does IAM help with compliance and audits?
IAM makes it easier to show who had access, why they had it, and whether that access was reviewed. Access logs, role management, and identity reports reduce manual effort during audits and help organizations meet regulatory requirements more consistently.
Can Zero Trust work in hybrid or legacy environments?
Yes. Zero Trust does not require everything to move to the cloud at once. Identity-first Zero Trust works across cloud and on-prem environments by applying the same access controls and identity policies regardless of where systems are hosted.
Where should organizations start if they want to adopt Zero Trust?
Most organizations should start with identity. Enforcing multi-factor authentication, reviewing privileged access, and implementing risk-based access policies can significantly reduce exposure to attacks. From there, Zero Trust can be expanded to devices, applications, and data.
How long does it take to see value from an identity-first Zero Trust approach?
Many organizations see immediate benefits once basic identity controls are strengthened. Reducing excessive permissions, improving visibility into access activity, and blocking risky sign-ins can have a measurable impact within weeks, not months.






Gotta try your luck somewhere, right? ilotto is another option for those lottery dreams. Go for it! ilotto
Honestly, 92games isn’t bad. It’s got a good variety of games to keep you busy. I like that it’s updated regularly. Have a look here: 92games
Trying to log in to pk777login now. Hopefully, it’s quick and easy. Hate when login processes are a pain. Wish me luck: pk777login