The way AEC firms work has changed dramatically. Cloud tools, AI-powered systems, and remote collaboration have become everyday essentials. They help your teams work faster, share ideas more easily, and keep projects moving, no matter where everyone is located.
But with all this convenience comes a real concern: keeping your intellectual property (IP) safe. Your blueprints, CAD files, and design models aren’t just files; they’re your firm’s competitive edge and, often, your client’s most sensitive information. If that data ends up in the wrong hands, it could damage your reputation, put legal contracts at risk, and lead to serious financial loss.
The good news? You can take control. In this blog, we’ll break down what IP protection really looks like for AEC teams in today’s digital-first world and how the right tools (like Microsoft Purview) can make the process simpler and more secure.
Table of Contents
Key Takeaways
- – AEC firms face unique IP risks due to remote work, cloud collaboration, and valuable design data.
- – Microsoft Purview offers a powerful yet simple solution to secure sensitive CAD, BIM, and blueprint files.
- – A strong IP protection strategy includes identity security, access control, data classification, and team training.
- – AI tools are useful, but must be implemented carefully to avoid exposing sensitive project data.
- – Proactive steps today can prevent data loss, protect client trust, and ensure compliance with industry standards.
Why IP Protection Matters in AEC
AEC firms handle highly sensitive and valuable assets. From design drawings to simulation models and client specifications, every digital file holds critical information. If any of it falls into the wrong hands or gets leaked accidentally, it can:
- – Put important client contracts and project deals at serious risk
- – Violate non-disclosure agreements
- – Cause reputational harm
Clients expect strict confidentiality and secure handling of their projects. A data breach could mean losing a client forever or being excluded from future bids.
Common Threats to IP in the Digital Era
Even well-meaning employees can unintentionally expose sensitive information. Here are some of the most common threats facing AEC firms:
– Unauthorized file sharing
: Accidentally sending blueprints via unapproved apps like WhatsApp or Gmail.
– Unmanaged devices
: Laptops or mobile devices accessing project data without proper security controls.
– Insider threats
: Disgruntled employees or contractors with access to proprietary files.
– Shadow IT
: Use of non-sanctioned tools for file storage or sharing.
– Phishing and malware
Hackers target design files through email attacks or infected USB drives.
The rise of remote work and BYOD (bring your own device) policies only increases these risks.
Legal Frameworks and Compliance Standards
AEC firms often work across jurisdictions and with public-sector or enterprise clients who require strict adherence to compliance standards. Relevant regulations and frameworks include:
- – ISO 19650: Standards for managing BIM data
- – U.S. Copyright Law: Protects original architectural works and designs
- – Non-disclosure agreements (NDAs): Legal obligations to protect client IP
- – State-level data privacy laws (e.g., California Consumer Privacy Act)
Failure to comply can lead to lawsuits, penalties, or lost contracts. Protecting your IP isn’t just a best practice; it’s a legal necessity.
Microsoft Tools That Help Secure Your IP
AEC firms can benefit greatly from using Microsoft Purview to protect their intellectual property. It offers a straightforward and effective way to safeguard sensitive architectural and engineering data, such as:
- CAD files
- BIM models
- Blueprints
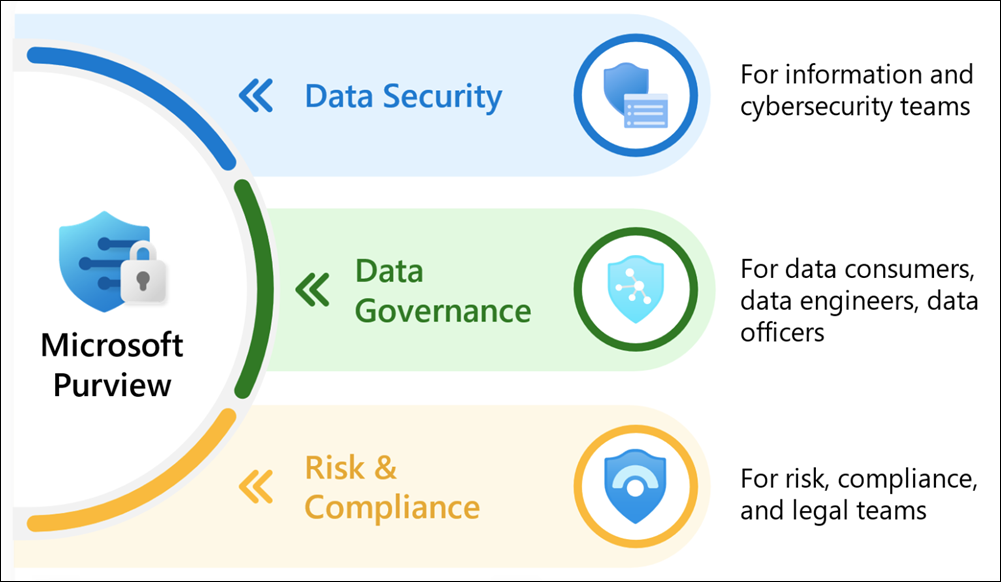
With Microsoft Purview, you can
- – Classify and label documents based on sensitivity.
- – Control access to ensure only the right people can view or edit critical files.
- – Track how data is shared and used across your organization.
It also supports compliance with standards like ISO 19650 and other regional data privacy laws, making it ideal for AEC environments where confidentiality and traceability are essential. For firms handling multiple collaborators and job sites, Purview provides a centralized way to manage and secure your most valuable digital assets.
Best Practices for AEC IP Protection
Technology alone isn’t enough. A strong security posture also requires well-structured policies and consistent execution. Here’s a simple and effective step-by-step process every AEC IT team can follow:
Step 1: Strengthen Identity Security
Implement Multi-Factor Authentication (MFA) for all users to prevent unauthorized access.
Step 2: Limit Access to Sensitive Files
Follow the principle of least privilege; only grant access to users who absolutely need it.
Step 3: Protect Critical Data
Apply Data Loss Prevention (DLP) policies specifically targeting CAD and BIM file formats.
Step 4: Secure External Sharing
Restrict file sharing to trusted domains and disable public sharing by default.
Step 5: Manage User Lifecycle
Ensure immediate offboarding of users after project completion or employment termination.
Step 6: Monitor and Audit Regularly
- Conduct frequent audits of file access and sharing logs to detect any suspicious activity.
Step 7: Educate Your Team
Train employees regularly on secure collaboration practices and their role in protecting IP.
By embedding these steps into daily workflows, AEC firms can create a culture of security that protects their intellectual property from both internal and external threats.
Role of AI & LLMs in Enhancing (or Risking) IP Security
AI brings opportunities and challenges to IP security:
How AI helps
- – Detects suspicious behavior like bulk file downloads.
- – Flags risky sign-ins from unusual locations.
- – Automates the classification of sensitive documents.
How AI can cause risks
- – LLMs like ChatGPT could expose confidential data if employees paste sensitive content into public tools.
- – Poorly trained AI models could retain sensitive project data.
Tips: Train your team to use AI responsibly. Use enterprise-grade tools with in-built privacy controls. Configure Microsoft Copilot with sensitivity labels to prevent data leaks.
Action Plan: What Your IT Team Should Do Next
Getting started with IP protection may seem overwhelming, but a structured approach makes all the difference. Here’s a clear, user-friendly roadmap for AEC IT teams:
Step 1: Start with a Security Assessment
Evaluate your current security posture, data flows, and areas of vulnerability. Simplicity IT offers this as part of our onboarding process.
Step 2: Locate and Classify Sensitive Data
Identify where your CAD, BIM, and other design files live, and determine who can access them.
Step 3: Implement Microsoft Purview
Use it to classify, label, and secure critical project data. Apply policies to ensure controlled access and visibility.
Step 4: Apply Identity and Access Policies
Enforce MFA, restrict access based on job roles, and ensure secure login practices across your organization.
Step 5: Set Up Secure Devices and Collaboration
Ensure all devices accessing your data are compliant, updated, and monitored. Limit collaboration tools to secure, approved platforms.
Step 6: Monitor, Report, and Improve
Track usage patterns, flag anomalies, and adjust policies with regular reporting and audits.
Step 7: Train Your Team
Human error is a top risk. Empower your employees with training on secure sharing, device use, and AI tool usage.
Following these steps helps your AEC firm create a proactive, scalable, and sustainable IP protection strategy tailored for modern cloud environments.
Final Thoughts
Protecting intellectual property is no longer optional for AEC firms. It’s a core business priority.
With hybrid work, AI, and cloud collaboration now the norm, your firm needs a modern, proactive strategy to secure your most valuable assets. Microsoft offers the tools to do just that, but it takes expertise and industry knowledge to configure them effectively.
Simplicity IT understands the unique needs of AEC businesses. Whether you’re dealing with ISO compliance, securing CAD workflows, or enabling secure collaboration across job sites, we can help you build a secure digital foundation.
Need help protecting your IP? Let’s start with a free security assessment customized for your firm’s needs.







Yo, jilibet bonus, you say? Who doesn’t love free stuff?! Seriously, check out jilibet for some sweet bonus offers. More chances to win, you know? Get your jilibet bonus jilibet bonus!
Looking for a new casino to try your luck? I saw someone mention yycasino and I’m curious! Looks like there are good offerings there! Find out here yycasino and get in the game!
Alright, so I’m trying to phdream register download. Anyone know where to find the official app? Don’t wanna get a virus or anything. Help a brother out! phdream register download
Okay, Vina24h com m… sounds interesting. Checking it out now! Hope it’s good stuff. See for yourself: vina24h com m
3333betcom… The name’s got a ring to it! Never played there before, but I’m always up for a new betting spot. Fingers crossed! Give it a look: 3333betcom
78king? Time to see if I can become the king of betting there! Wish me luck, folks! Let’s roll: 78king